u003cstrongu003eThere are so many different blogs about a security baseline. This is not just another one, this one is specifically for those who really want to be secure. This first blog is focussing on all of the different parts of a solid security baseline for your entire infrastructure and cloud. This blog also only focusses on the Microsoft Cloud and other products of theirs.u003c/strongu003e
A security baseline for your company
- Security
- 23 november 2023
- 7 min leestijd

u003ch2 class=u0022wp-block-headingu0022u003eWhat is a security baseline?u003c/h2u003ernWell, as far as Cloud Agent is concerned, it’s a least minimum security measure for any business making use of certain services like Microsoft 365, Azure and other Microsoft services. The security baseline, which is implemented by Cloud Agent for our customers, is mainly for security-consious organizations in which – for example – standard users don’t have any administrative rights. In many cases the baseline is in line with the recommendations from Microsoft.rnrnBecause every company, even non-business related accounts, face security threats. However, the types of security threats that are of most concern differ from one organisation to another. That’s why this blog focusses on the bare minimum that is applicable for any company.rnu003ch2 class=u0022wp-block-headingu0022u003eThe security baselineu003c/h2u003ernBecause this blog is just a simple overview of the security baseline implemented by Cloud Agent, it will not go into much detail in this blog. However, the points discussed in this blog will be further expanded on in seperate blogs which will be linked here.rnu003ch2 class=u0022wp-block-headingu0022u003eA password policyu003c/h2u003ernA password policy has been discussed many time on so many blogs, this blog will not go into detail. The point to get across is to at least have a password policy. Even though Cloud Agent encourages our customers to make use of at least a strong password with a authenticator as a second step (Multi-Factor Authentication) and u003cstrongu003enotu003c/strongu003e to make use of a SMS or Voice for the second step, Cloud Agent does recommend to make use of u003ca href=u0022https://www.microsoft.com/en-us/security/business/solutions/passwordless-authenticationu0022 target=u0022_blanku0022 rel=u0022noopeneru0022u003epasswordless authenticationu003c/au003e. The following picture illustrates the many different ways to authenticate.
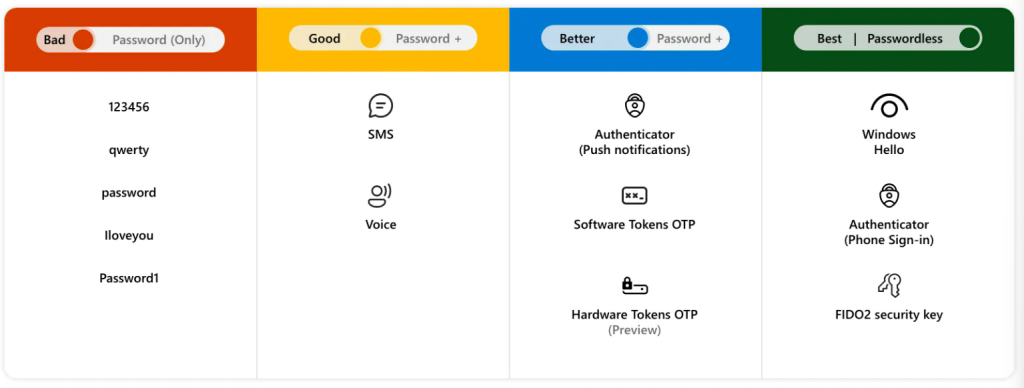
u003ch2 class=u0022wp-block-headingu0022u003eBasic Authentication or Legacy Authenticationu003c/h2u003ernBasic Authentication, also known as Legacy Authentication is a way of authentication that does not support Multi-Factor Authentication. Meaning, it does not support the user to perform a second step after providing the username and password to login.rnrnYou might understand why this is a great way for malicious people to hack an account, because after acquiring the victim’s password there will be no need to also get a hold of the victim’s second step authentication method like his or her phone.rnrnu003cstrongu003eCloud Agent never allows this usage u003c/strongu003eexcept in really monitored exceptions like for example a legacy application. The problem however is that starting from the u003ca href=u0022https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/block-legacy-authenticationu0022 target=u0022_blanku0022 rel=u0022noopeneru0022u003e1st of October 2022 Basic Authu003c/au003e will be disabled for all Microsoft 365 tenants, meaning the companies still making use of this method will have no other choice but to mitigate and/or migrate to a better solution – which is Modern Authentication.rnu003ch2 class=u0022wp-block-headingu0022u003eMulti-factor Authentication (MFA)u003c/h2u003ernIt goes without mention these days that MFA should at least be enabled for all users without exception, well there are exceptions but this will be explained in detail in a more detailed and dedicated post.rnu003ch2 class=u0022wp-block-headingu0022u003eUp-to-date operating systemu003c/h2u003ernVirtual Machines, Desktops, Laptops, no matter what kind of device it is there needs to be a policy in place to make sure the OS is up to date with the u003cstrongu003eCritical and Securityu003c/strongu003e updates.rnrnIn most cases Cloud Agent manages the devices using Intune with a RMM tool to support it. The Modern Workplace provided by Cloud Agent has default policies to u003ca href=u0022https://docs.microsoft.com/en-us/mem/intune/protect/windows-update-for-business-configure#windows-10-feature-updatesu0022 target=u0022_blanku0022 rel=u0022noopeneru0022u003eenable patchmanagementu003c/au003e. The additional RMM tool makes sure that every other (virtual) machine is getting their updates on a regular basis.rnu003ch2 class=u0022wp-block-headingu0022u003eBring Your Own Device (BYOD) policiesu003c/h2u003ernJust about everyone has a personal device, like a smartphone and a laptop, which (in many cases) is also used for business purposes. For example, employees have Microsoft Teams installed on their own device to be able to chat and/or call with co-workers. Or simply have Outlook configured on their phone. A huge issue used to be to convince the employees to manage their personal devices if it’s being used for business purposes. The main reason has always been that the user does not know what the IT department can see on their device.rnrnA great alternative, a real must have these days, is to make use of u003ca href=u0022https://docs.microsoft.com/en-us/mem/intune/apps/app-protection-policiesu0022 target=u0022_blanku0022 rel=u0022noopeneru0022u003eApp Protection Policiesu003c/au003e provided by Microsoft Endpoint Manager (also known as Intune). It protects the corporate data even if the app contains both corporate and personal data, which is the almost always the case.rnrnCloud Agent makes sure that a few default policies are in place when a user wants to make use of their own personal device to access company data. The policy protects the data by encrypting it, protecting it with a PIN and removes the company data from the phone when needed. These policies makes sure that your company data is secure on a device not known and/or managed by the company and makes a clear destinction between personal and company data.rnu003ch2 class=u0022wp-block-headingu0022u003eProtecting your devices, account and datau003c/h2u003ernDevices, owned by our customers make have to be protected. Cloud Agent makes use of Microsoft Defender to protect devices and to quickly act on any threats by monitoring them proactively.rnrnThis subject will be discussed in a more detailed post.rnu003ch2 class=u0022wp-block-headingu0022u003eTo concludeu003c/h2u003ernThis subject is vast and can contain many pages but we chose not to do that and give an overview of the bare minimum that needs to be in place.rnrnTo summarize;rnu003culu003ern tu003cliu003eYou want to have all users enabled for MFA;u003c/liu003ern tu003cliu003eYou do not want to allow Legacy Authentication;u003c/liu003ern tu003cliu003eYou want to protect your data, your mails, your account and devices;u003c/liu003ern tu003cliu003eOperating Systems need to have the monthly Security and Critical updates applied;u003c/liu003ern tu003cliu003eCorporate data on personal devices need to be protected.u003c/liu003ernu003c/ulu003e
